What Armadillo and Themida does
A compiled AutoIT exe consists of two
parts: the ‘real Exe’ or the interpreter part aka Aut2Exe\AutoItSC.bin and the
compiled script, that is a normal *.a3x that was just attached to this
‘Aut2Exe\AutoItSC.bin’. Packer like UPX just compresses the
‘Aut2Exe\AutoItSC.bin’ part, but must leave the attached *.a3x(sometimes also
called overlay data) untouched. Armadillo also compress/encrypt the *.a3x part
so how that is possible?
Well it hooks(intersects) the APIs(=functions window provides to very program)
Aut2Exe\AutoItSC.bin normally use from Windows to load the attached *.a3x. In
detail these are the APIs CreateFile, ReadFile, SetFilePointer and CloseFile
from Kernel32.dll.
So how this plays together?
1. The Armadillo hook on CreateFile checks if the exe opens it self and if that is the case it memorise this file handle (= some ID Windows gives you when you open a file) that is used by the ReadFile hook on determine if AutoIt reads from the exe.
2. The ReadFile hook checks -in cause the exe is opened it self- the position AutoIT likes to read from. When it reads above the end of the Autoit-exe on the disk, it just decrypts/decompress the *.a3x data in memory and streams it into the return of read file.
3. The interpreter part receives the uncompressed *.a3x data just as normal an can process…
Furthermore Armadillo also hooks SetFilePointer to keep track of possible changes in the start position for readfile and closeFile is hooked to know when read is finished(=close) and it can discard the file handle.
Fortunately this data lays in memory in one piece so we can easy dump it with ollydebug or winhex.
Identifying Armadillo:
Look for the string “.pdata” at the start of a File:

Note: ‘.pdata’ as PE-Section is also common for normal 64-bit exe so that is just a weak mark
Look for the String “PDATA000”
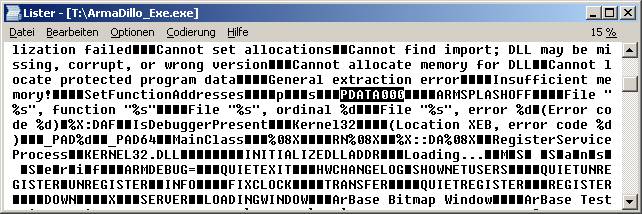
Armadillo uses that to mark its protected/packed data.
Identifying Themida/WinLicense:
Look for „WinLicen“ in the Exe header
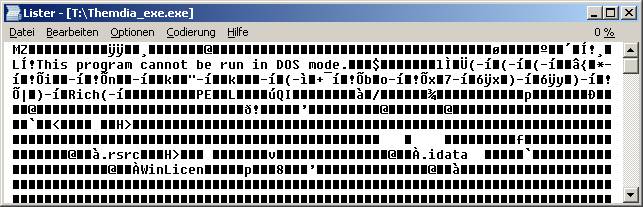
Of course that can be easy change – there are better ways of detect for ex. the program PEiD.
However so far to that part. J
Dumping OverlayData of Armadillo/Themida with Winhex
http://free.pages.at/pepspace/Winhex_15.4.7z
Dump with Winhex only works if the app stays open and don’t quit right after it was started.
1. When the app is running start Winhex. Press alt+F9 to bring up the RAM tab.
open the entired RAM of the process(in case there are two the one with the higher PID)
2. press ctrl+PageDown to go to the very end of the RAM. Press ctrl+F to bring up the Text search dialog and enter “EA06” and as direction search “upwards”.
3. Press Alt+2 to mark the end of the selection as you see in the screenshot
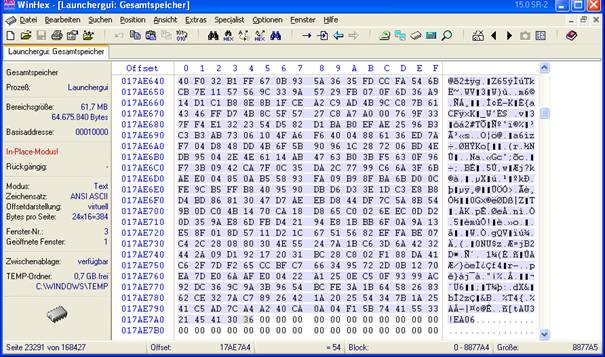
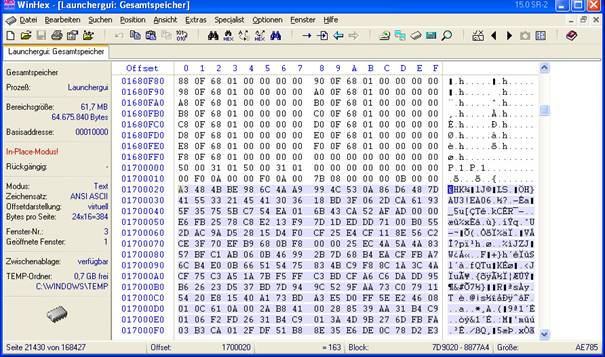
Press F3 to find next EA06. From ‘EA06’ got
back 16(=0x10) Byte to include normal AutoIt signature that looks like this:
0003DBF0 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 ................
0003DC00 A3 48 4B BE 98 6C 4A A9 99 4C 53 0A 86
D6 48 7D £HK¾˜lJ©™LS.†ÖH}
0003DC10 41 55 33 21 45 41 30 36 AB 99 D0 DE 88 5E 49 DF AU3!EA06«™ÐÞˆ^Iß
There press Alt+1 the mark the beginning of the selection.
4.Press ctrl+shift+n to save the selection to a new file. Name it ‘dump.a3x’ and you should be able to run it with AutoIT if you have installed it (and associated it with *.a3x files)
Or use that script:
///////////////////////////////////////////////////////////////////
// Winhex Template File
//
// Purpose: Extract Compiled AutoIT Script data from and AutoIT exe
// Usage: (Copy this script in Winhex and name it ‘AutoItExtract-EA06.whs’)
//
Run Winhex RAM-Edit(Alt+F9) and select the running AutoIT-exe,
// [select entire Memory]
// Press Enter to bring up StartupCenter and run script from there
//
// Download regged Winhex: http://free.pages.at/pepspace/Winhex_15.4.7z
// Move to EOF
Assign EOF GetSize
Dec EOF
Goto EOF
// Find upwards & mark end
Find "EA06" Up
IfFound
// Include match (CurrentPos+3)
Assign a3x_End CurrentPos
Assign a3x_End (a3x_End+3)
// Find upwards & mark start
Find "EA06" Up
IfFound
// Move to AutoIT Header begin(CurrentPos-0x14)
Assign a3x_Start CurrentPos
Assign a3x_Start (a3x_Start-0x14)
// MarkBlock
Block1 a3x_Start
Block2 a3x_End
// Save to AutoIt Exec File
CopyIntoNewFile "myDumped.a3x"
Else
MessageBox "Error: Second EA06-Marker not found!"
EndIf
Else
MessageBox "Error: First EA06-Marker not found!"
EndIf
However it’s important to know how to do it without script and the idea/concepts behind. Also imagine that script will do it some malicious user ‘hacks’ the AutoIT Script so that there is no ‘EA06’. :)
…and with Olly Debug
RE-Pack with ollydbg & winhex
http://free.pages.at/pepspace/myTools.exe
1. Enable the Protection against ‘OutputDebugString exploit’ option in
Hide Debugger v1.2.3f by Asterix(Plugins\HideDebugger.dll) as you see below
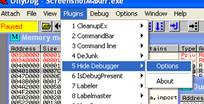

…else armadillo will make ollydebug to crash when you run it.
If you don’t see the ‘Plugins’ in the menu bar, check the path to the
Plugin Dir in Options\ Appearance\[Directories]
2. Load the Exe that is packed by Armadillo by dragging it into ollydbg, File/Open or with F3. Then press F9 to run it.
Incase you get an exception like this press Shift+F9 several time to pass it to the program
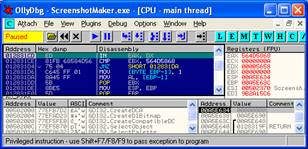
Until the program runs(runs&quit)
To avoid pressing Shift+F9 all the time open the options(alt+o)/[Exception], Enable ‘ignore the following exceptions’ and then click on the ‘Add Last Exception’
3. Press Alt+M to open the Process Memory Window.
Double click on the .text section of the Exe you loaded (it’s nearly always loaded at address 0x00401000). Ensure that there is something else than only 00’s… to ensure that app was successfully unpacked. Close this dump window.
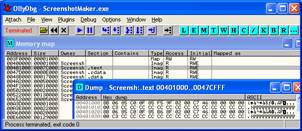
In the Process Memory Window press Alt+L to
bring up the search window

Enter ‘EA06’ as search string. Then press ctrg+L to find next .(Don’t miss to
switch back from the dump window to the Process Memory Window before you press
ctrl+L) until there are no more matches.
For dumping use the last dump windows there you found ‘EA06’ as you see on the screenshot. The type of that memory region should be ‘Priv’ate.

4.Dumping(Saving the RAM data to disk) is done like this:
Right click in the dump window and choose Backup/Save data to file.
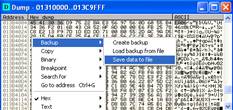
Now the save as dialog box come up, where you can save the data.
That’s drag the *.mem into myAutToExe and hope that now it can be decompiled correctly.
Thermida AntiDebug Specs
(Just ignore this if you've never step though asm code with an debugger)
Checks first byte of an API for 0xCC
^- so avoid setting a breakpoint directly to for ex. CreateFile (instead set on the next instruction in CreateFile)
\\.\NTICE \\.\SICE \\.\SIWVID [No comment] ;)
"ntice.sys" [No comment] ;)
"iceext.sys" Numega Softice Extension for hiding softice
"Syser.sys" Syser Kernel Debugger (http://www.sysersoft.com)
"HanOlly.sys" from 'HanOlly_edition_for_themida_1.9'
"extrem.sys" "FRDTSC.SYS" standardname of 'PhantOm'plugin for Ollydebug (change this in Ollydbg.ini![Plugin PhantOm]!)
"Filem" "REGMON" "regsys" "sysregm" "PROCMON" yaya the powertools from Sysinterals
HKEY_LOCAL_MACHINE\SOFTWARE\NuMega\DriverStudio